According to statistics, 43% of hacker attacks became possible due to flaws in the software architecture. This means that nearly half of all programs are developed without a thorough check of system security quality. Such neglect in ensuring robust security measures can lead to significant financial and reputational damage for companies. For example, Google was fined $50 million for non-compliance with the General Data Protection Regulation (GDPR), demonstrating the high stakes of inadequate security practices.
Clearly, ensuring software security is critical for both end-users and the companies developing the software. Development teams should implement rigorous testing, including automated security testing tools, to identify vulnerabilities early and strengthen the product’s defense. Security testing tools help by simulating various attack scenarios, ensuring that any potential loopholes are addressed before a product goes live.
Different security testing tools serve various purposes—some focus on vulnerability scanning, while others specialize in penetration testing or risk assessment. Make sure to select the tool that aligns with your specific security requirements.Mykhailo PoliarushCEO, ZappleTech Inc.
Zapple Tech specialists have shared valuable insights into the various security testing tools available and how to select the best one for the specific requirements of your project. These tools are crucial in mitigating security risks and ensuring compliance with industry standards. By leveraging the right automated security testing tools, companies can safeguard their software and avoid the consequences of overlooked vulnerabilities.
Table of Contents
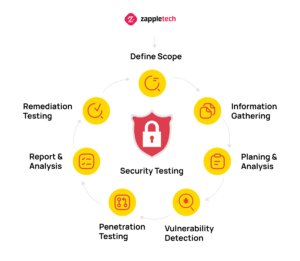
What is Application Security Testing
Application security testing is a set of tests aimed at identifying vulnerabilities within the app’s architecture that could expose it to potential security risks. Unlike functional testing, which focuses on ensuring the software works as intended, security testing is designed to evaluate how well the application can resist potential hacker attacks and protect sensitive data from unauthorized access.
When conducting security testing, it’s essential to use advanced security testing tools or automated security testing tools to streamline the process. These tools help identify common weaknesses in the system’s security infrastructure and highlight areas for improvement, making the testing procedure more efficient.
QA engineers focus on several key objectives during the process:
Identifying the primary protection target. Understanding which parts of the application are most critical to protect, such as user data or system access points.
Checking for software vulnerabilities. This involves using security testing tools to detect weak points in the system. Vulnerabilities like poor user authentication processes or operating system malfunctions can expose the software to significant threats.
Risk assessment. Security testing aims to forecast potential risks to the system. By using automated security testing tools, testers can simulate various attack scenarios to assess the damage potential and mitigate risks before they impact the business.
Troubleshooting vulnerabilities. While security testing doesn’t directly fix issues, it provides detailed reports with recommendations on how to resolve them. These reports allow developers to monitor progress and ensure vulnerabilities are adequately addressed.
By leveraging automated security testing tools, organizations can enhance their security testing process, ensuring a robust defense against potential threats and delivering a more secure final product.
Types of Application Security Testing Tools
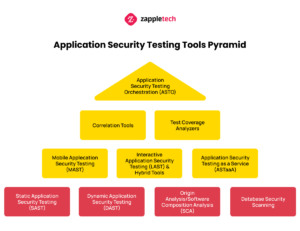
Consider 10 approaches to finding bugs in code that can lead to program security failures. Some of them are considered constitutive. Let’s consider them first.
Static App Security Testing (SAST)
Finding bugs in code during the early stages of program design is essential for testers aiming to reduce the cost of fixing vulnerabilities later in the development process. Static Application Security Testing (SAST) is a method that plays a crucial role in this effort. SAST is an automated security testing tool that allows developers and testers to scan the source code for vulnerabilities even before the application is fully developed or deployed. By detecting issues early on, teams can address security flaws before they become more difficult and costly to fix.
The approach used by SAST falls under the “glass/white box” or “white hat” method, meaning it analyzes the application from an insider’s perspective. Both QA engineers and ethical hackers, or “white hat” testers, have access to the system’s internal structure, allowing for a thorough review of potential security weaknesses. Automated security testing tools, like SAST, are highly effective because they offer early feedback, reducing risk by identifying security vulnerabilities in code as it’s written.
By integrating security testing tools like SAST into the software development life cycle (SDLC), organizations can ensure their applications are resilient against various attack vectors, ultimately leading to more secure and robust software products.
Dynamic App Security Testing (DAST)
Origin Analysis/Software Composition Analysis (SCA)
Database Security Scanning
Data storage systems, although not always integral to a program, are deeply interconnected with application operations. Applications rely on the data within these databases, and databases, in turn, depend on the activity of the programs they support. Therefore, security testing tools specifically designed for databases are crucial to maintaining the integrity and security of sensitive data.
Database Security Scanning (DSS) tools work with databases in a static state, meticulously scanning for vulnerabilities such as weak passwords, misconfigurations, and excessive administrative privileges that could lead to security breaches. By identifying these issues early, organizations can prevent potential threats that might compromise sensitive data.
Incorporating security testing tools early in the development process helps identify and address vulnerabilities before they become bigger issues. This proactive approach saves time, money, and potential security risks later.Mikhail BodnarchukCDO, ZappleTech Inc.
In addition to DSS, automated security testing tools have become essential for streamlining this process. These tools enable teams to automate regular scans and tests, ensuring continuous database security without requiring constant manual intervention. As the testing teams’ skills evolve, they can implement more advanced automated security testing tools to further enhance the security measures protecting their databases.
Interactive App Security Testing (IAST) and Hybrid Tools
Interactive Application Security Testing (IAST) and hybrid tools represent a modern approach to ensuring the security of applications. These tools combine both static and dynamic testing methodologies to provide a more comprehensive assessment of potential vulnerabilities. By actively testing applications in real-time while they are running, IAST hybrid tools go beyond traditional static analysis, which only examines code at rest, and dynamic analysis, which tests applications in operation.
These hybrid tools, often referred to as automated security testing tools, offer significant advantages, especially in Agile and DevOps environments. By integrating both static and dynamic methods, they ensure that security testing happens throughout the software development lifecycle, identifying vulnerabilities that might be missed by standalone static or dynamic testing. This dual approach also reduces the likelihood of false positives, which are common in traditional security testing tools.
Additionally, automated security testing tools, including IAST, provide continuous feedback, allowing developers to address security risks early and efficiently. This helps teams keep up with the fast-paced development cycles typical in Agile and DevOps workflows, making hybrid security testing tools a more efficient alternative to static application security testing (SAST) and dynamic application security testing (DAST).
Mobile App Security Testing (MAST)
Mobile apps are increasingly exposed to a variety of security risks, such as unauthorized access to sensitive customer identification data, misuse of the platform, insecure mobile communications, and more. As mobile applications play a vital role in business operations, ensuring their security has become paramount. This is where automated security testing tools come into play, making it essential to thoroughly test mobile applications, including their security aspects, to protect against potential threats.
Mobile Application Security Testing (MAST) tools are designed to offer comprehensive testing solutions that go beyond traditional testing. While MAST tools are similar to other security testing tools that assess programs in both static and dynamic states, they include features tailored specifically for mobile environments. These features help mitigate the risk of data breaches by detecting vulnerabilities that could allow unauthorized code injections, either on the client or server side, without needing access to the app’s source code.
By incorporating automated security testing tools like MAST, businesses can better protect their mobile apps from a wide range of security threats, ensuring data security and maintaining user trust.
App Security Testing as a Service (ASTaaS)
App Security Testing as a Service (ASTaaS) offers a comprehensive approach to safeguarding your applications without the need to build a complex, in-house security infrastructure. By leveraging automated security testing tools, businesses can effectively analyze vulnerabilities and ensure robust protection against potential threats. These security testing tools provide features such as static application security testing (SAST), dynamic application security testing (DAST), API validation, and risk probability analysis. Additionally, ASTaaS services often include penetration testing, where cyber-attack models are simulated to assess the strength of your defenses. This approach allows organizations to focus on other critical areas while relying on trusted third-party providers for essential security measures.
Correlation Tools
QA engineers often face the challenge of dealing with false positives or false negatives in their testing results, which can significantly impact the accuracy of assessments. Correlation tools play a crucial role in addressing this issue. These tools help reduce the noise in data, allowing for a more precise analysis of the information generated during testing.
They not only provide comprehensive access to reports and data from various automated security testing tools but also allow engineers to compare and evaluate the performance of different security testing tools in a streamlined manner. Although many correlation tools focus primarily on aggregating data from other tools, some also offer integrated code review features, enhancing their overall utility in ensuring secure and reliable software.
Test-Coverage Analyzers
Test-Coverage Analyzers are crucial in understanding the effectiveness of your testing processes by evaluating which parts of the code have been thoroughly examined during tests. They provide valuable insight by calculating the percentage of code lines or available paths that have been tested. This percentage helps teams identify gaps in their test coverage and improve the overall robustness of their security testing tools. Setting an optimal test coverage percentage beforehand allows teams to compare the results with the ideal standards, ensuring more comprehensive test coverage.
Test-Coverage Analyzers can function independently or be integrated into Static Application Security Testing (SAST) tools. These automated security testing tools are designed to ensure that the codebase is thoroughly checked for potential vulnerabilities, leaving no section untested. Incorporating such tools as part of your security strategy not only enhances the detection of issues but also helps in maintaining a higher level of code integrity and security across the development lifecycle. By integrating automated security testing tools, organizations can ensure that their security testing tools provide consistent, accurate, and efficient results.
.
App Security Testing Orchestration (ASTO)
Due to the constant growth of the number of programs and the transition from one technology to another (e.g., from classical web products to microservices), available security testing tools are also growing rapidly. It is not uncommon for multiple tools to test a single product. In such situations, the Application Security Testing Orchestration, or ASTO, comes to the aid of testers. This tool helps to centralize the data management and reporting of all ASTs that run in a particular development environment.
Guidelines for Selecting Software Testing Tools Types
If you choose in favor of quality control of the security of the software you create, this is already a huge step towards success. Indeed, according to statistics, about 30,000 Internet resources are subjected to cyberattacks every day.
Now it is important to analyze which tools are right for your project. We have prepared some recommendations for you.
- It is better to start security testing using constitutive tools (DAST, SAST, SCA, DSS).
- If you created the program or if your developers have access to its source code, give preference to SAST.
- If third parties write the program and you do not have access to its source code, use DAST.
- In open-source programs, test with SCA tools.
Summarizing
As digitalization expands, businesses increasingly rely on software to manage sensitive data and operations. This growing reliance on technology exposes organizations to numerous security risks, making it essential to adopt advanced measures to safeguard applications from cyber threats. Automated security testing tools are vital in this effort, as they provide continuous monitoring, identifying potential vulnerabilities early in the development process. By automating these tasks, companies can improve efficiency, reduce manual errors, and ensure that their applications meet stringent security standards.
Security testing tools also help organizations maintain compliance with industry regulations by identifying weaknesses that could lead to data breaches or unauthorized access. From vulnerability scanning to penetration testing, these tools offer a comprehensive approach to protecting critical assets. Investing in these solutions not only strengthens security but also instills confidence in customers, knowing their sensitive information is protected.
Use automated security testing tools to ensure ongoing monitoring and real-time detection of threats. Automation minimizes human error and keeps your applications safe from evolving security risks.Sergey AlmyashevCOO, ZappleTech Inc.
At Zapple Tech, our experts specialize in integrating top-tier automated security testing tools into your software development lifecycle. Whether you’re dealing with financial data, healthcare information, or legal records, we ensure your applications are fortified against emerging threats. Partner with us to secure your software from malware, cyber-attacks, and unauthorized access, keeping your business operations safe and uninterrupted.